Understanding the steps in a social engineering attack: from reconnaissance to covering tracks
Social engineering attacks are becoming increasingly common, and they’re rarely immediately obvious. Here’s a breakdown of the cycle attackers use to exploit human behavior and steal information.
“It’s critical that… organizations take steps to protect themselves [from social engineering attacks]… by being informed about the different types of attacks and how they work. ”
Defining a social engineering attack
Social engineering attacks are malicious attempts to “hack” human psychology to trick individuals into divulging sensitive information, fulfilling an action, such as downloading malware, or giving an attacker access to a network or system. Social engineering attacks attempt to exploit the target’s trust, fear, or urgency, to manipulate them into breaking security protocols.
Social engineering attacks specific to email come in a number of different forms, including phishing, spoofing, spear phishing, and whaling.
Importance of understanding the attack cycle
With a recent study showing that 75% of respondents believe social engineering threats and phishing attacks are the biggest danger to their organization’s cybersecurity, it’s important to understand the cycle of a social engineering attack to better protect your organization:
Proactive Awareness: Understanding the cycle of an attack ensures individuals and organizations are more aware of the threat that exists, enabling them to take steps to protect themselves by implementing security protocols, like DMARC, properly training employees, and investing in technology to detect and prevent attacks.
Early Detection: The 2021 Cost of Data Breach Report identified that the average time to identify a breach was around 287 days, with a further 56 days taken to contain it once detected. Understanding the cycle of an attack ensures organizations can be vigilant and detect suspicious behavior or malicious attempts to gather information before an attack is carried out.
Response and Mitigation: If a breach occurs as a result of a social engineering attack, it’s important that organizations have a plan in place to mitigate the damage. Understanding the cycle of an attack assists organizations with the development of a response plan with protocols that address each stage of an attack in an efficient and effective manner.
From reconnaissance to covering tracks
To better protect yourself and your organization from a social engineering attack, it’s important to familiarize yourself with the steps of an attack’s cycle. Skip to the infographic
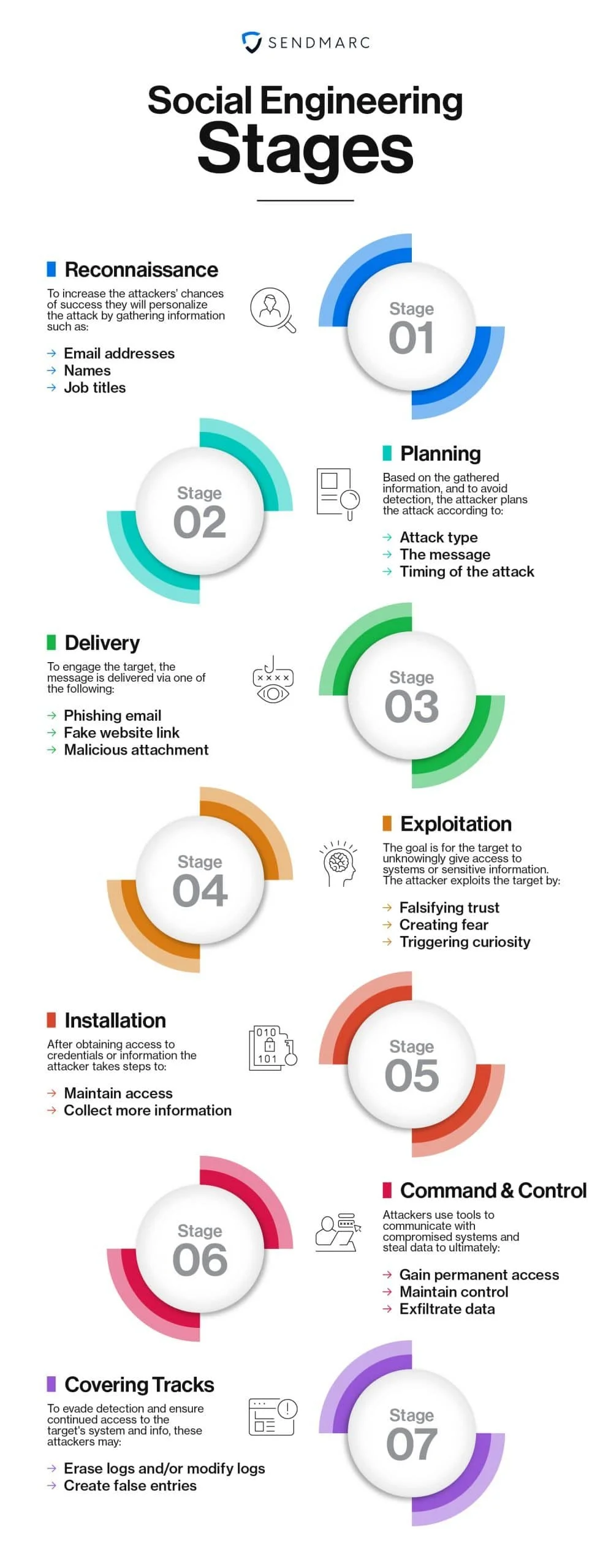
Reconnaissance: The initial stage of any social engineering attack which involves the gathering of information about the target by a potential attacker. The information gathered can include email addresses, names, and job titles. By gathering this information, the attacker develops a detailed understanding of the organization and how to personalize the attack to make it more convincing and increase its chances of success.
Planning: Once the attacker has gathered enough information, they can work on planning their attack. This usually involves deciding on the type of attack, crafting its message, and identifying the best time to launch. By tailoring the attack using detailed information, the attacker increases the chance of success, while minimizing the risk of detection.
Delivery: At this stage of an attack, the message (also referred to as a “payload”) is delivered. It could be in the form of a phishing email, a link to a fake website, or a malicious attachment that contains malware. This is the point when the target is first engaged.
Exploitation: Once the target takes the required steps, as instructed by the message, their trust, fear, or curiosity is exploited. The desired result is for the target to fulfil the actions identified in the message and unknowingly give the attacker access to systems or sensitive information.
Installation: Once the target has provided credentials, downloaded malware, or given the attackers access to systems, networks or information, the attacker takes whatever steps are required to maintain persistent access and gather more information. Attackers can silently access a system or network for months before an actual attack is carried out, as demonstrated by the SolarWinds supply chain attack where hackers gained access to the SolarWinds Orion software update and inserted a backdoor to monitor and collect data. It’s believed they gained access to the system as early as September 2019, and remained undetected for over a year.
Command and Control: Command and Control (C2) tools are used by attackers to communicate with the compromised system or to steal data. Once they’ve established permanent access, they will use these tools to exfiltrate data or maintain control over a comprised system.
Covering Tracks: To cover their tracks while carrying out malicious actions, attackers may erase or modify logs and other evidence to make it more difficult to detect that an attack has occurred. They may also create false or misleading log entries to throw investigators off. This is one of the most crucial stages for the attacker because it helps to ensure they maintain persistent and undetected access to the target’s system or information.
Prevention is the best defense
Given the challenges of detecting and containing breaches caused by social engineering attacks, one of the best defenses is prevention. By understanding the stages of the cycle of an attack, you and your organization can take steps to identify and mitigate the risks posed by these threats.
DMARC is a powerful tool for preventing social engineering attacks by preventing email spoofing and protecting your organization against phishing attacks. It provides a proactive way to authenticate email messages and enforces policies that prevent unauthorized senders from using your domain names in email messages.
By implementing DMARC alongside other best practices for email security, you reduce the risk of social engineering attacks, while protecting your sensitive information and resources. Reach out to us today to learn how we can help.
This article is originally published on Sendmarc. Click here to read the original article.